Check out the EPAS website at www.epas.de or continue reading to find out more.
It is an established fact that insecure, reused, and compromised passwords are one of the leading causes of security breaches.
When we consider the future of password security, we are often told that the only way to secure passwords is to either replace them with alternative technologies or at least supplement them with additional factors.Without dismissing the benefits of modern authentication technologies, we aim to challenge this popular statement and examine the practical reasons that led to it.
A password alone is not inherently an insecure method of authentication. Like any other IT component, it requires testing and quality assurance to ensure it is secure.
The issue with passwords has been, until now, the lack of testing solutions, specifically to simulate the actions of an attacker attempting to crack them.
This was not due to a lack of password-cracking tools, but because revealing the plaintext password results in a privacy breach.
EPAS offers a unique approach by identifying and preventing insecure, reused, and compromised passwords without breaching users’ privacy.
This enables organizations to effectively eliminate all password-related vulnerabilities while continuing to use a proven, well-known, and well-supported authentication method.
EPAS is patented technology used on thousands of servers and identity management systems by several million enterprise users, in over 30 countries. Since using EPAS, none of these accounts have been reported as compromised because of insecure passwords.
Using extra security measures like MFA and risk-based authentication is still recommended to increase security. However, this can often be challenging, especially for legacy and OT systems or when the necessary technology changes lead to very high costs.
The implementation can also take a long time, leaving accounts open to password-related attacks.
Even when MFA is used, the password is usually one of the factors and must be properly secured.
EPAS provides immediate protection, for all passwords, whether used as the only factor or part of MFA. The EPAS appliance is set up within 24 hours, even in complex environments, and provides instant results, without installing any software on protected systems.
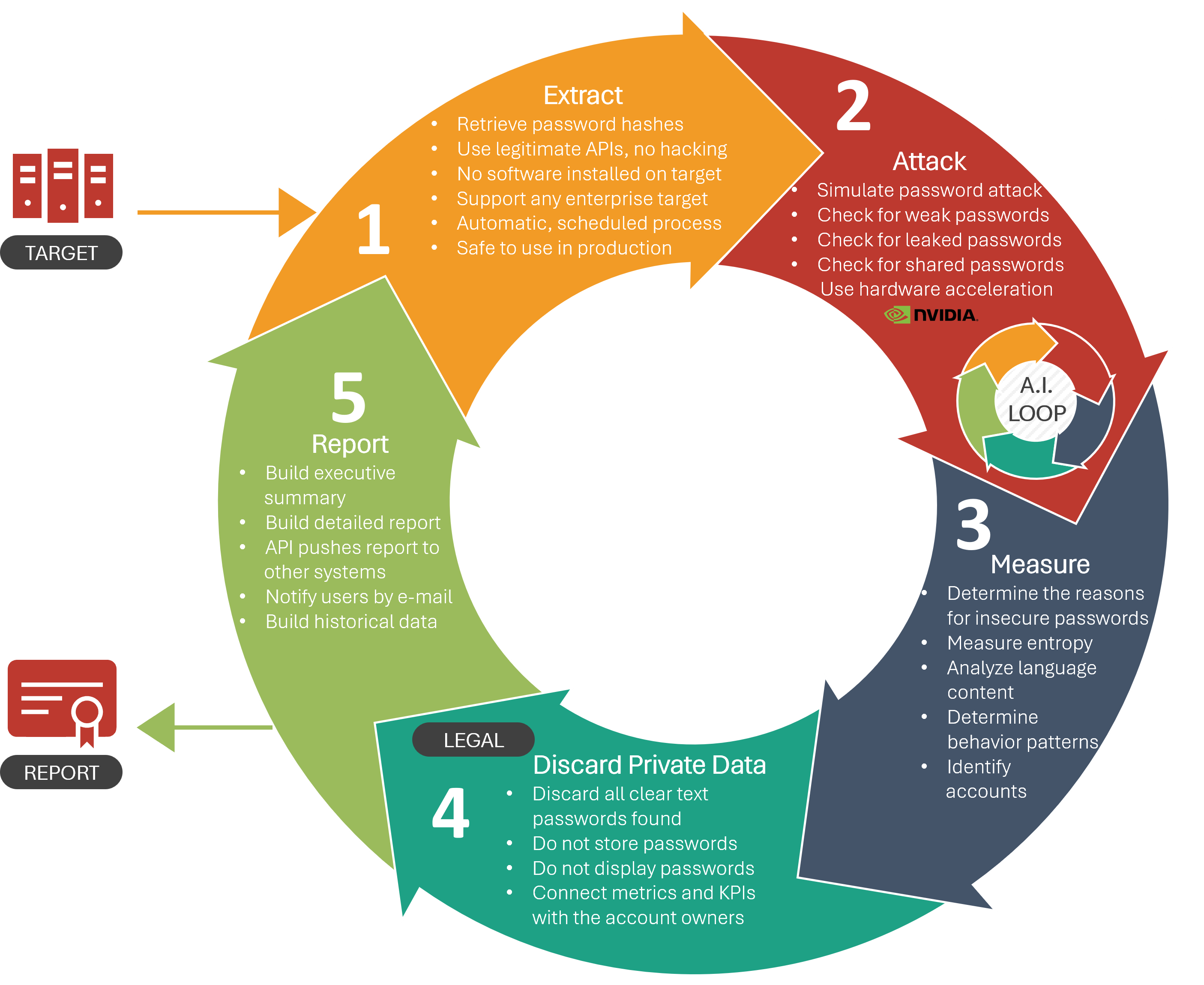 |
SCAN FOR INSECURE PasswordsEPAS Audit represents the first solution to successfully address the challenge of conducting privacy-compliant password security assessments while simulating authentic attacks. |
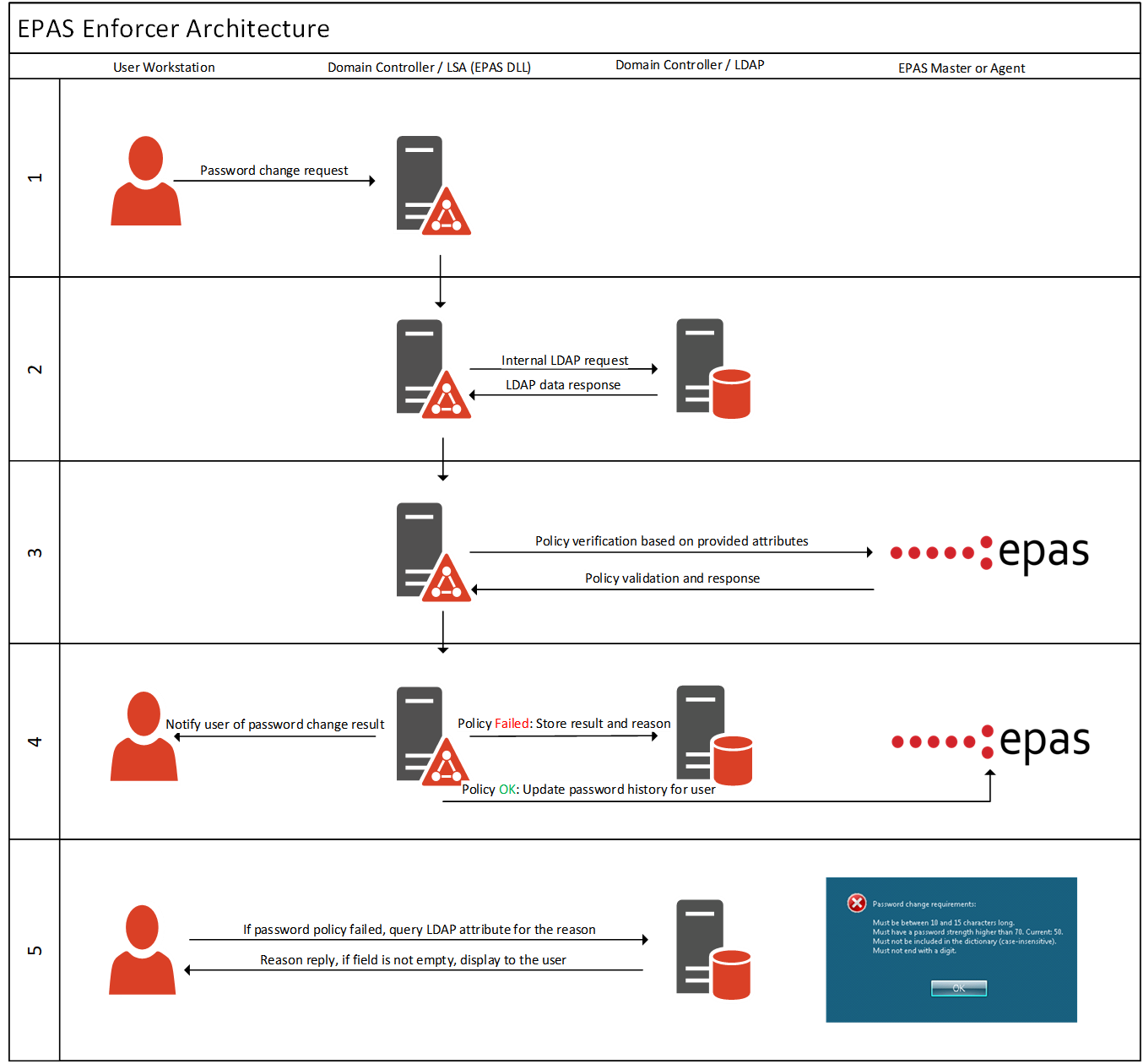
PREVENT INSECURE PasswordsEPAS Enforcer offers an essential toolset to leverage the results and metrics produced by EPAS Audit, ensuring that insecure passwords are used again by blocking them during password changes. |
 |
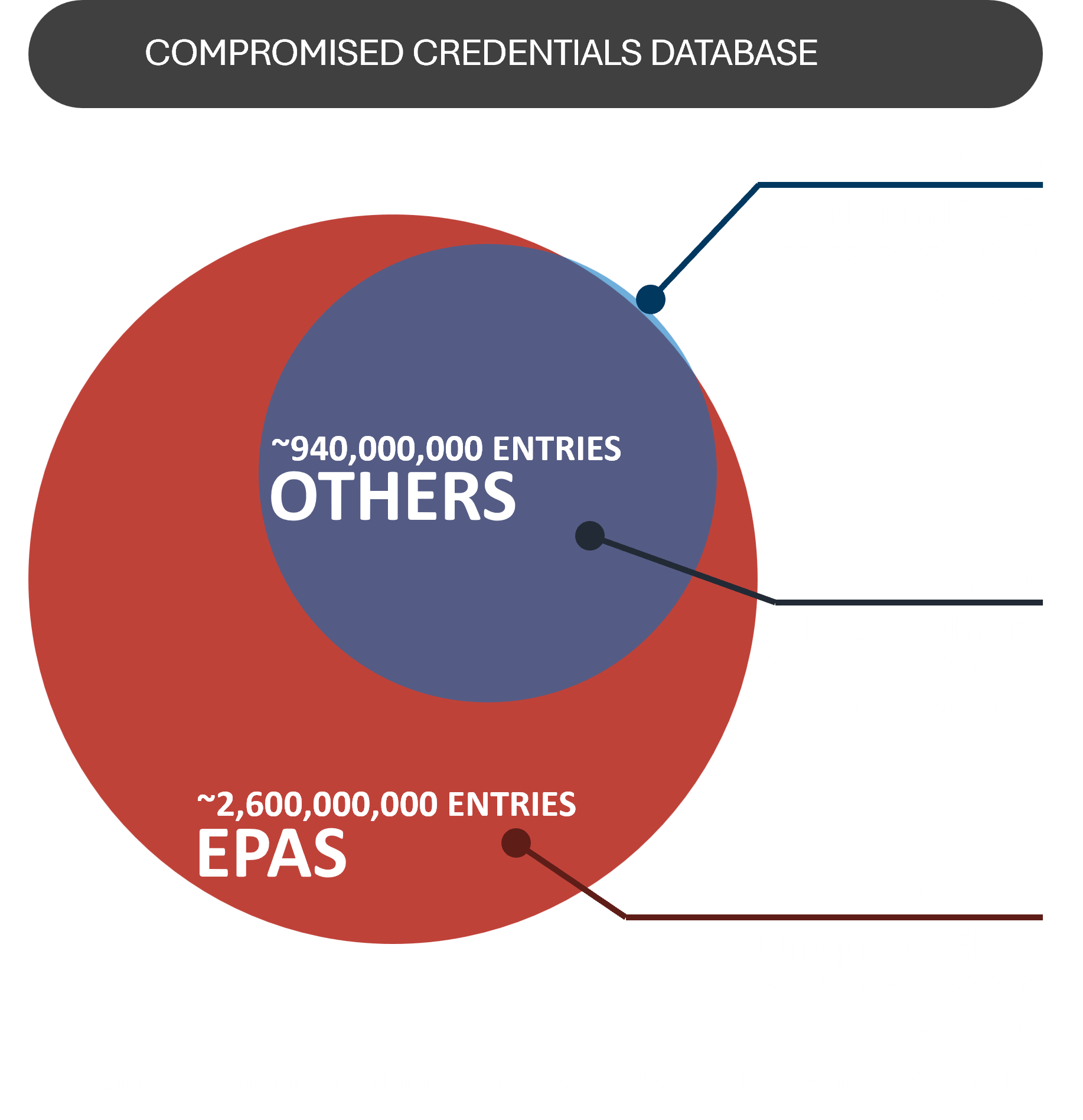 |
Vast Password Intelligence SourcesCompromised credentials represent the most frequently exploited attack vector in password-related breaches. EPAS offers one of the largest and best curated password intelligence databases available today, utilized to both identify and prevent the use of compromised credentials. |
Artificial Intelligence EnabledAdvanced criminals and state actors are increasingly using artificial intelligence to perform password attacks. EPAS employs AI to detect passwords vulnerable to such attacks. |
 |
 |
Governance, Risk, and Compliance SupportWhether for enhancing security, remediation, or meeting regulatory standards, EPAS reports offer complete visibility into vulnerable credentials. |
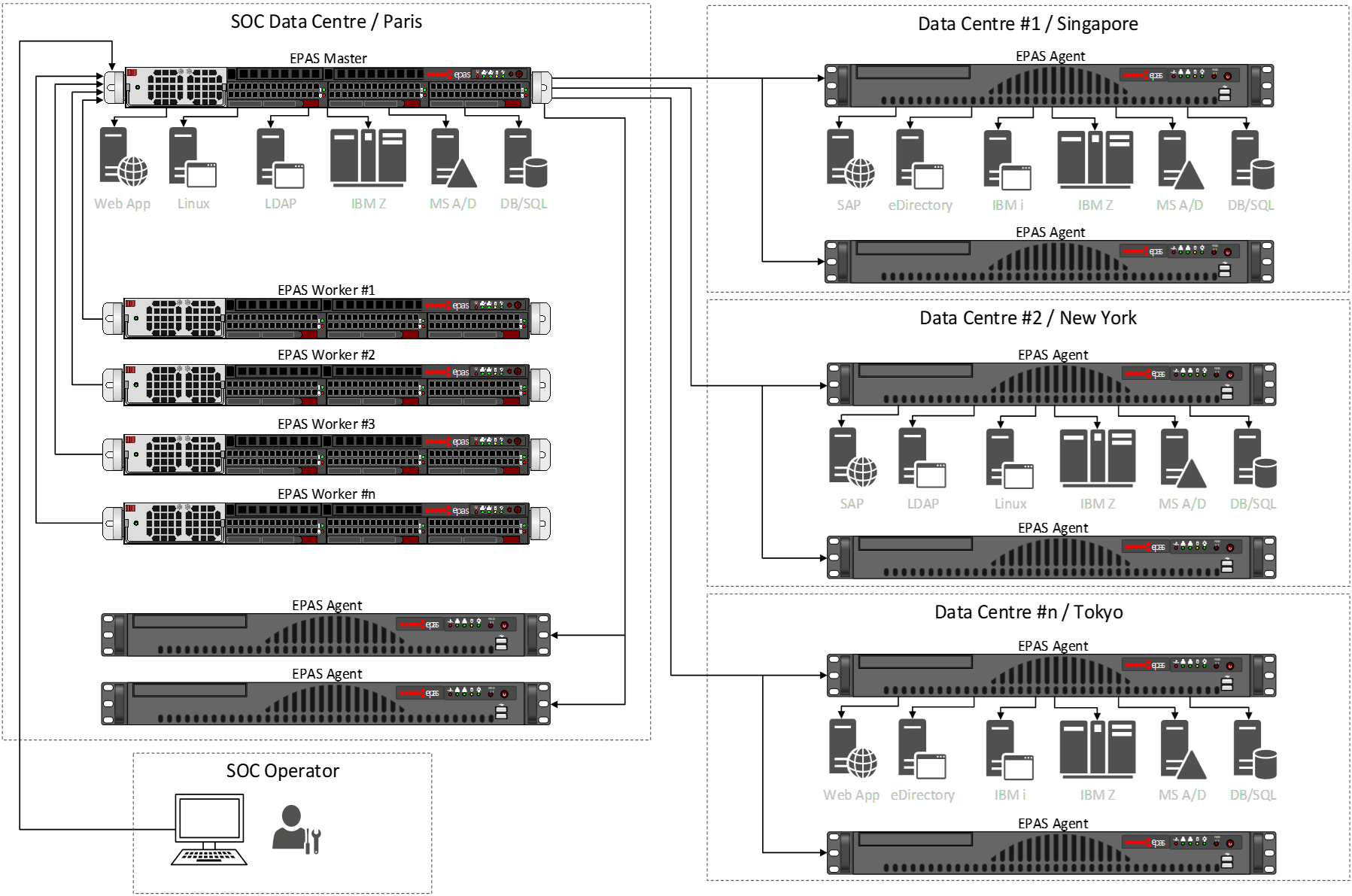
Highly ScalableEPAS is routinely deployed across multiple data centers, and across multiple countries. |
 |
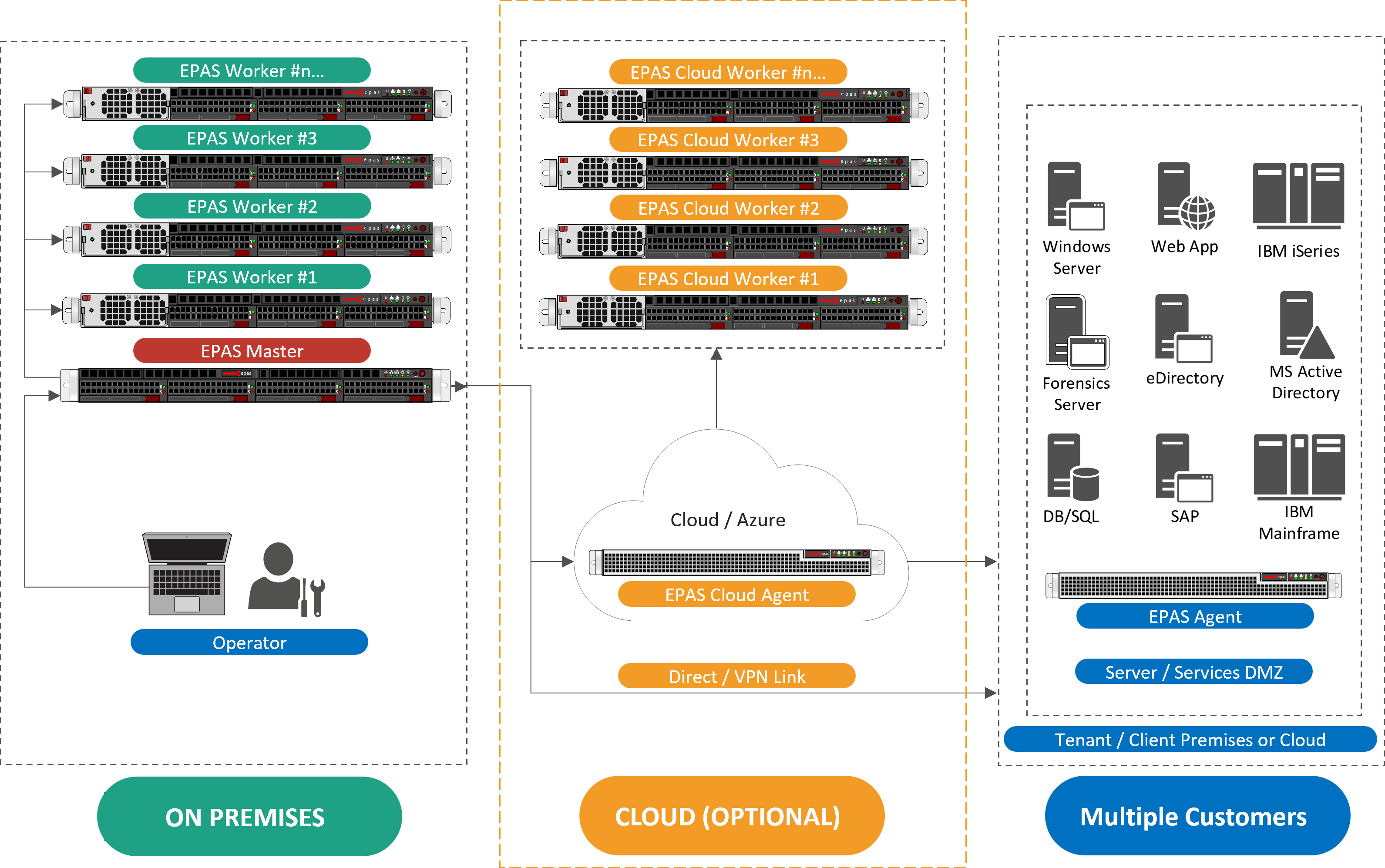 |
Cloud EnabledEPAS is an on-premises or private cloud appliance solution. It can be deployed in single data centers to accommodate smaller enterprises or can be scaled up as required, extending across multiple data centers or locations, serving single or multiple tenants from a centralized location. |
Security by DesignEPAS handles sensitive information, including user credentials and hashed password data. To guarantee the security of this data against external attacks as well as malicious internal use (e.g., modifying the system to display recovered passwords), the EPAS platform employs full encryption, TCG (Trusted Computing Group) technology sealing, independent and internal security testing, and follows a secure development process within a certified environment. |
 |
Core Capabilities
|
Enterprise Integration
|
Use Cases & Benefits
|
Security Features
|
EPAS Audit Supported Systems
|
|
EPAS Enforcer Supported Systems
|
Hardware & Virtualization
|